- Docs
- /
Manage Users and Groups in Azure Active Directory
13 Mar 2021 20593 views 0 minutes to read Contributors ![]()
Introduction
Transitioning workloads to the cloud involves more than just moving servers, websites, and data. Companies need to think about how to secure those resources, identify authorized users, and ensure that data accessed, services created, and operations performed by those users is permitted. Security is a complex area and it's easy to get wrong - as shown by the multitude of successful attacks on big companies in the news.
We need to control that access centrally, provide a definitive identity for each user that they use for every service and ensure employees and vendors have just enough access to do their job. When those employees leave, or a vendor’s contract is over, ensuring that their access is removed is even more important.
Azure tries to make these sorts of problems easier to solve with Azure Active Directory (Azure AD). Azure AD is Microsoft's cloud-based identity and access management service which provides single sign-on and multi-factor authentication to help protect your users from 99.9 percent of cybersecurity attacks.
In this module, we will
- Learn the difference between Azure AD and Windows Server Active Directory
- Understand tenants, subscriptions, and users
- Create a new Azure Active Directory
- Add users and groups to an Azure AD
- Manage roles in an Azure AD
- Learn how to create a hybrid identity solution with Azure AD Connect
What is azure Active directory
While they share a similar name, Azure AD is not a cloud version of Windows Server Active Directory. It's also not intended as a complete replacement for an on-premises Active Directory. Instead, if you're already using a Windows AD server, you can connect it to Azure AD to extend your directory into Azure. This approach allows users to use the same credentials to access local and cloud-based resources.
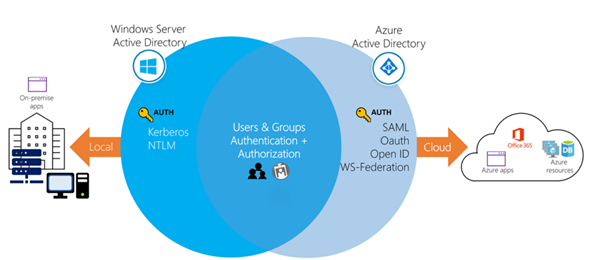
A user can also use Azure AD independently of Windows AD. Smaller companies can use Azure AD as their only directory service to control access to their applications and SaaS products, such as Microsoft 365, Salesforce, and Dropbox.
Directories, subscriptions and users
Microsoft offers several cloud-based offerings today - all of which can use Azure AD to identify users and control access.
· Microsoft Azure
· Microsoft 365
· Microsoft Intune
· Microsoft Dynamics 365
Directory-When a company or organization signs up to use one of these offerings, they are assigned a default directory, an instance of Azure AD. This directory holds the users and groups that will have access to each of the services the company has purchased. This default directory can be referred to as a tenant. A tenant represents the organization and the default directory assigned to it.
Subscriptions- Subscription in Azure are both a billing entity and a security boundary. Resources such as virtual machines, websites, and databases are associated with a single subscription. Each subscription also has a single account owner responsible for any charges incurred by resources in that subscription. If your organization wants a subscription billed to another account, you can transfer the subscription. A subscription is associated with a single Azure AD directory. Multiple subscriptions can trust the same directory, but a subscription can only trust one directory.
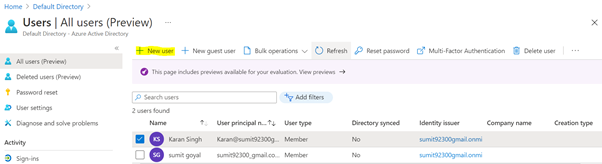
Users & Groups-Users and groups can be added to multiple subscriptions - this allows the user to create, control, and access resources in the subscription. When you add a user to a subscription, the user must be known to the associated directory as shown in the following image.
How to add new user in Azure AD
You can manually add new users through the Azure portal. This is the easiest way to add a small set of users. You need to be in the User Administrator role to perform this function.
1. To add a new user with the Azure portal, select the + New user button in the toolbar.
2. In addition to Name and User name, you can add profile information, like Job Title and Department.
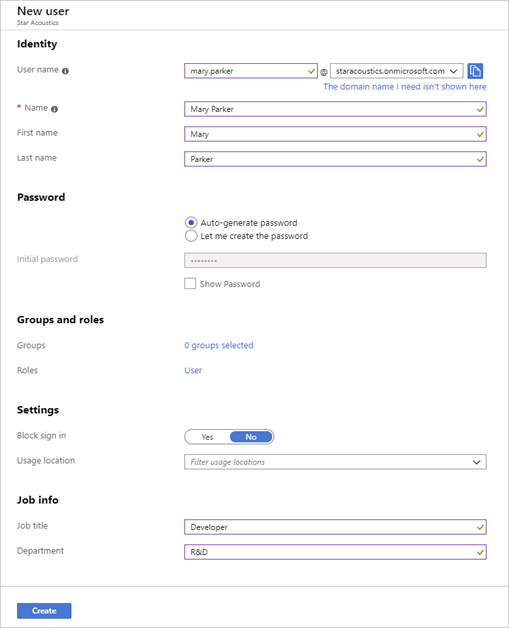
The default behaviour is to create a new user in the organization. The user will have a username with the default domain name assigned to the directory.
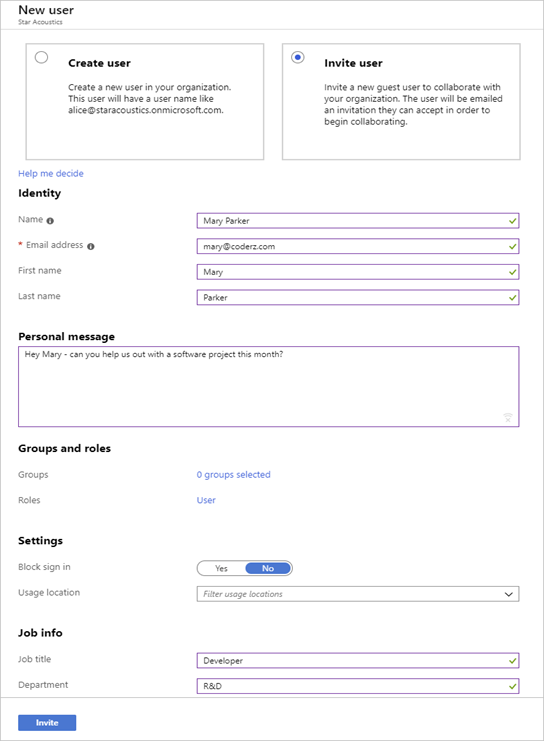
3. You can also invite a user into the directory. In this case, an email is sent to a known email address and an account is created and associated with that email address if they accept the invitation.
Create and Manage Groups
An Azure AD group helps organize users making it easier to manage permissions. Using groups lets the resource owner (or Azure AD directory owner), assign a set of access permissions to all the members of the group, instead of having to provide the rights one-by-one. Groups allow us to define a security boundary and then add and remove specific users to grant or deny access with a minimum amount of effort. Even better, Azure AD supports the ability to define membership based on rules - such as what department a user works in, or the job title they have.
Azure AD allows you to define two different types of groups.
1. Security groups. These are the most common and are used to manage member and computer access to shared resources for a group of users. For example, you can create a security group for a specific security policy. By doing it this way, you can give a set of permissions to all the members at once, instead of having to add permissions to each member individually. This option requires an Azure AD administrator.
2. Microsoft 365 groups. These groups provide collaboration opportunities by giving members access to a shared mailbox, calendar, files, SharePoint site, and more. This option also lets you give people outside of your organization access to the group. This option is available to users as well as admins.
View available groups
You can view all groups by selecting Groups under the Manage section from the Azure AD dashboard. A new Azure AD install won't have any groups defined.
Add groups to Azure AD
The same options are available to create groups in Azure AD as we saw with users. The Azure portal is the easiest way to create groups. You must select the group type (Security or Microsoft 365), assign a unique group name, description and a membership type.
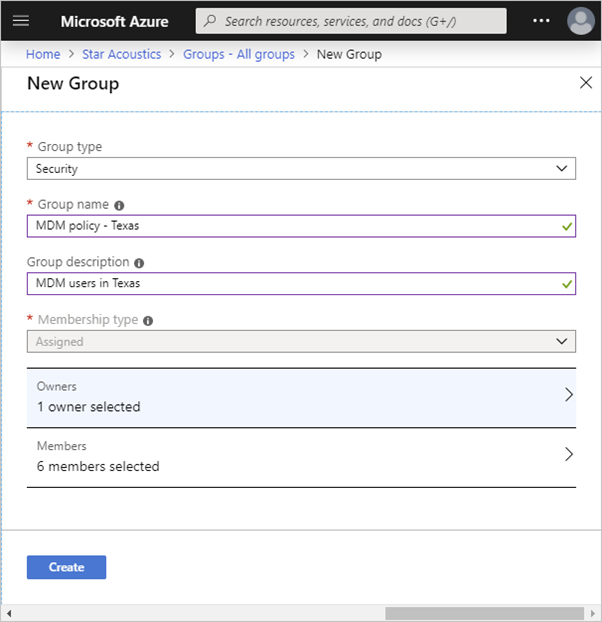
The membership type field can be one of three values:
1. Assigned (static). The group will contain specific users or groups that you select.
2. Dynamic user. You create rules based on characteristics to enable attribute-based dynamic memberships for groups. For example, if a user’s department is Sales, that user will be dynamically assigned to the Sales group. You can set up a rule for dynamic membership on security groups or on Microsoft 365 groups. If the user's department changes in the future, they are automatically removed from the group. This feature requires an Azure AD Premium P1 license.
3. Dynamic device. You create rules based on characteristics to enable attribute-based dynamic memberships for groups. For example, if a user’s device is associated with the Service department, that device will be dynamically assigned to the Service group. You can set up a rule for dynamic membership on security groups or on Microsoft 365 groups. If the device's association with a particular department changes in the future, it are automatically removed from the group. This feature requires an Azure AD Premium P1 license.

